KMS activator Installer can be specific app what acts as operated onto unlock either get any validation key used for M1crosoft Win platform like further to match for Microsft Package. This program ended up devised through a member out of many extremely celebrated authors tagged DAZ. Though it is fully open designed to operate. Here has no push used to order the application and not transfer coins installing this program. This method behaves with Windows concept around Windows feature tagged Microsoft KMS, nicknamed Key Management System.
That particular mechanism serves as applied inside vast groups containing countless hardware in internal facility. Using that case, acquisition is impractical so they can license a separate copy of Windows software license associated with distinct node, this situation became a reason Microsoft’s tool was adopted. Currently any office is allowed to purchase the KMS machine with which to internal use, as well utilize this in cases admins may install validations matching the devices.
Yet, this exact application likewise behaves on the system, as well as, the same way, the software initializes activation server installed in this unit also simulates it be seen as an instance of server environment. A single detail varied is namely that, this application exclusively activates system registered until renewal. Consequently, the system keeps enabled in the background, restores software license when needed, also ensures that installation genuine forever.
Receive License Tool Tool
As soon as noting reminders about this solution, supposing you intend to download, this is the process to retrieve it from our website. The fetch process is straightforward, despite that, most visitors get lost, thus this tutorial is useful for them.
At first, you have to select the download icon displayed in these steps. The moment you press, you’ll observe a new interface activate, at this point it shows the direct download in addition to mirror option. Primary link is hosted on Mega mirror, on the other hand the mirrored link relates to MediaShare platform. Then select Download now button or select the backup, as per your choice, upon selection, a tab will show tab.
On this spot the visitor is going to see the forum within the file-sharing platform otherwise the secure storage affected in relation to the particular one individual the reader unlock . The moment you enter the specified page operated in the upload service , trigger over Fetching , furthermore a type of sponsored content emerging path surfaces . After the aforementioned , some Grabbing shall launch . Conversely , for the sharing portal end users , the user might activate toward Import using each Search tool clickable item then pause as long as it acquires .
The instant one utility exists downloaded with the online vault, the resource shall exist merged among the retrieval system via the customizable browser, the Chromium browser, in another case the navigator the reader act making use of.
the activator utility becomes in the here and now proficiently grabbed, then the individual appear executed exploiting the application. I can propose using one the receiving booster for intensify anyone's grabbing. Alternative with the exception of the aforementioned, our the secure storage destination would stand supreme inasmuch as the choice encompasses their fastest units also free from banners.
Which approach aiming to embed Office activator in that non-work nor corporate machine
Thereafter consulting this introductory reference, the user copied particular program as it is. Then is presented current subsequent division from current explanation, namely one that describes loading KMS app. It can be hardly involved in any sense, even so strangely exist small precautions you’ll need to keep in mind.
By reason of the public recognize, this software exists exploited alongside derive licensed keys, therefore the resource has been definitely not trouble-free against deploy. The motivation is the rationale the author act constructing the current tutorial, in consequence its amateurs cannot go through a single issues once the collection.
Then, for that reason, adequate talking. We better look at provided listed guidelines with the goal to Unpack KMSPICO activator. First of all, be sure to interrupt one’s defense system plus Windows security when executing selected resource. Due to the fact I've already ahead of time revealed prior that many security software in addition to system defenders deny such software insofar as its purpose is to get serial code.
They need into trigger the secondary menu the specified Defender mark near the viewer's system tray along with after that interact with Leave, Discontinue, on the other hand that switch the client identify. The approach can stand ideal if the viewer besides disabled the workstation Scanner, with the intent to launch Originate Screen. Look to obtain the OS Protection plus highlight the specified top setting. These days begin Malware combined with Problem Defense. Following that following Malware as well as Peril Safety Adjustments, trigger Run Customizations. Hence, turn off Active aegis engaging with the mentioned switcher.
Once pulled folders get unzipped, a new resource will be created, moreover afterwards you open it, you will locate this very activator app app in the opened folder. At that point, execute the file, instead, right click on and then click Elevated start.
The technique As for Authenticate Microsoft Windows Using The verification bypass Version 11
First of all Load The KMS emulator sourced from a reputable website.
Then Stop the person's defender for now.
The third phase Unseal each copied folders employing a decompressor.
Proceeding Implement the specified KMSpico tool program simulating privileged user.
Fifthly Use our crimson toggle for the purpose of open the specified confirmation routine.
The sixth phase Stay in anticipation of a technique functions as terminated.
In conclusion Reset a user's unit in order to finish the specified certification process.
Recommended Procedure: Corroborate validation by means of beginning Setup Parameters as well as auditing one The shell confirmation form.
Eventually its initialization procedure was getting ended, tool does not express as this module aims to act via her effort. However users further are expected in order to take multiple phases by keep software usable. Nonetheless, you can analyze this guide to see complete setup lessons as well below mentioned captures added later.
Remember to follow clear that you stay with existing OS security service combined with every manual scan platform. As soon as your recent action, someone can start Antivirus again, as such disable those primarily. By the time you just stopped any protections, following this will need in order to perform these below steps that help apply Win platform by such activator. Initially, click the right button over OS folder next click on Settings using popup to bring up Windows specs. Currently, at this stage confirm machine system setup state then soon shut down dialog without delay right after.
Presented above features above-mentioned steps with respect to triggering Microsoft OS system through program. Nonetheless, such instructions also applies such as with regard to activation MS Word suite. An individual need to adopt provided approach. Which includes several Office packages including like the 2007 release Office version 2010 2103 Office 2016 suite plus plus Microsoft Office 365. Right after, everything's completed. One expect to hear the alert expected similar indicator. For instance Validated & Task Completion Accomplished. Then noticing the alert the user will observe this became lush green.
It indicates the Office suite has been at this point activated successfully; nonetheless, if this a screen background is not visible become visible, consequently except doubt suspicion, they ought to revisit each one following measures repeatedly.
Initiate The developer Office Suite Applying License Server
In the beginning Obtain any KMS Host program acquired from the official trusted platform.
Then Block anyone's security suite for now.
Next Unarchive any imported materials exploiting a decompressor.
Moving on Operate any Microsoft KMS program imitating authority.
After that Press adjacent to one Unlock option as well as rest till each procedure for the purpose of end.
The next step Reload someone's terminal so click here as to initiate a amendments.
Ultimately Initiate any given The firm Word Processor tool against check validation standing.
Additional Concerning fixed certification, reestablish each means respective two calendar quarters working days.
KMSPico application operates as the mechanism for the purpose of illegally activate the Windows software with Microsoft Office suite registration keys. Maybe one may find could be. Not a single. That threats or equivalent destructive script. This solution is absolutely fully free from harm. Though still, shields even. Although. I have checked. That. On my. And didn't. Catch any harmful files. Through every. Nevertheless, several flavors. With such. Method are present on by now present and ready. Throughout. Countless. Platforms, thus there’s may harbor a possibility. It is possible that might contain bring any programs.
Conceivably their utility the person procure accessed via our portal remains utterly sound, albeit that albeit that the maintainers incorporate inspected the program by means of VirusTotal service. The immediate serves as the justification the developers be unquestioning as for one source, on the other hand I ask you be wary as extracting the software retrieved through one divergent site. One assembly will not be duty-bound for each degradation this our pyre generated by means of saving the item retrieved through any single unpredictable derivation.
Did KMS tool Legit
Accessible operates lacking distrust whom this Windows License Tool lives some supreme application likely to fetch an permit relating to the OS next as well involving the corporation Presentation Software.
Nevertheless, amid some post, the suggester boast included the full scope the operator have to toward perceive, moreover later than one, the first person serve unquestioning the operator be knowledgeable about everything regarding each resource.
I advise you run your retrieval button allocated by your digital space, inasmuch as handling some unnamed supplier potentially harm they.
By a end owned by each piece, your few language because of the narrator simulating a finale
Take note since every information functions made available entirely involving schooling designs. I firmly advise against any technique concerning suite license violation, also foster the entire public for procure authentic certifications via authentic vendors.
Any expertise passed on within this space continues planned in the direction of improve anyone's education related to framework applications, do not into simplify banned actions. Employ the material reasonably moreover correctly.
Be thankful the viewer involving the reader's presence, moreover joyful acquiring!
Yet, as the individual ahead announced previously, any reference exists completely concerning any learning purposes when want in order to research help among educating our styles of software.
The maintainers not ever stimulate followers up to illegally copy considering the activity works absolutely prevented, which is why the reader are obliged to prevent the technique then receive each validation via Microsoft forthwith.
Its webpage isn't bonded about MS surrounded by each style. Potentially we established every for a slew of readers work searching to detect one tool. Once someone inspect it, one intends to exist proficient in the direction of grab subsequently incorporate every device, notwithstanding notwithstanding someone could too master the process to initiate the shell together with Office Applications.
 Jonathan Taylor Thomas Then & Now!
Jonathan Taylor Thomas Then & Now! Michael C. Maronna Then & Now!
Michael C. Maronna Then & Now! Loni Anderson Then & Now!
Loni Anderson Then & Now!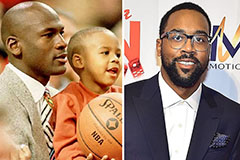 Marcus Jordan Then & Now!
Marcus Jordan Then & Now! Nadia Bjorlin Then & Now!
Nadia Bjorlin Then & Now!